Documentation
Active Directory support
XorMon natively supports AD and LDAP authorisation.Navigate to UI ➡ Settings ➡ LDAP Navigate: UI ➡ Top-right ➡ Settings ➡ Other ➡ LDAP and setup connection to your directory service
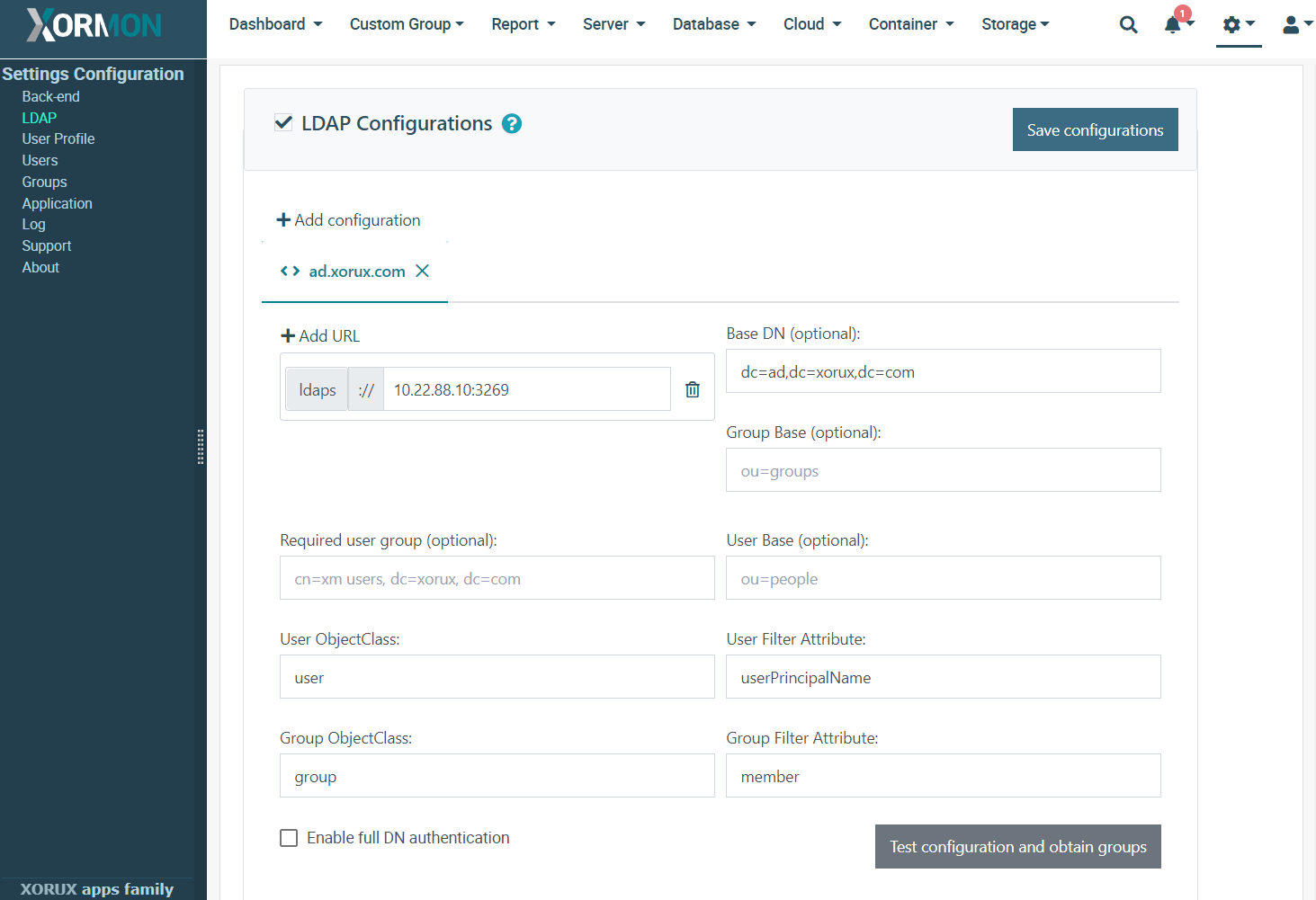 |
Click on + Add Configuration button and name new configuration.
Multiple configurations can be in use with precedence from left to right (re-order by arrows next to configuration name).
Login service first tries to authenticate user against local account in Xormon.
If not successful, it continues with LDAP configurations when enabled.
Directory Server
Enter LDAP URI with correct matching of protocol scheme and port number: e.g.ldaps:// for 636 (default if no port specified) or 3269 (preferred)
ldap:// for 389 (default if no port specified) or 3268 (preferred).
Multiple URIs can be specified for single configuration, but same protocol scheme must be used.
Optional: Enable redirects
If global catalog ports (3268, 3269) cannot be used and LDAP redirects need to be resolved, enable following:Edit config/application.properties next to xormon.war (usually in /opt/xorux/xormon) or create it from application.properties.template if not exists by renaming it.
Uncomment line with spring.ldap.base-environment.java.naming.referral = follow
Note that this may slow down LDAP access.
Attributes
Enter Base DN for all LDAP operations (e.g. dc=ad,dc=xorux,dc=com) or leave empty if full domain information is present in username (e.g. username@ad.xorux.com) and differs per user.Optionally enter Group Base to restrict group listing to only this subtree.
Optionally enter User Base to restrict access to users only in this subtree.
Optionally enter Required User Group to allow login only to accounts with assigned group specified by this full DN.
Specify User ObjectClass value identifying user objects (e.g. user).
Specify User Filter Attribute name corresponding to login username (e.g.
userPrincipalName for usernames like user@ad.xorux.com or sAMAccountName for Windows NT 4.0 logon names like ad\user).Specify Group ObjectClass value identifying group objects (e.g. group).
Specify Group Filter Attribute name which lists users within group (e.g. member)
Specify Group Filter Attribute name which lists users within group (e.g. member).
Username prefix/postfix allows you to skip domain part of username in login fields.
UserPrincipalName can be found from sAMAccountName logon name by:
ldapsearch -LLL -H ldap://your.ad.hostname -D 'yourdomain\yourusername' -W -x -b 'dc=your,dc=ad,dc=base' '(&(objectClass=user)(sAMAccountName=yourusername))' userPrincipalNameIf command is not found then install openldap-clients under root:
yum install openldap-clients